Note: The title looks grammatically wrong, but the term is "enforcing" is correctly used here.
These commands are here for reference to my guided tutorials.
Problem
In a basic Linux system, each file and folder (or directory) is allowed the access by the owner, group or others. And this access is further controlled into permissions of being able to read(r), write(w) and executable(x). I will refer to the term file to include folders unless mentioned otherwise. Users and programs can change owners and permission of files, if they have the permission to do so. The system typically divides the users into 2 groups;
- root = Linux Administrator
- user = Every other user who is not an administrator
If everyone and every program can change their own settings, eventually there will be a chance of creating security hole. Common approaches for security includes (1) restrict user to certain file permissions (use of groups are common) and (2)processes are further restricted in a "chroot" jail. Even with all this, the root user will have trouble controlling breaches due to user file permissions as these users still can change their file permission to allow everyone.
There are 2 approaches to change SELinux policies, here I will be looking at compiling the policy as a module.
SELinux basics
A set of file policies is introduced in Linux where every file is denied and a series of exceptions to access files is built is what makes SELinux work. All logs are by default to /var/log/audit/audit.log and where it may be in any one of the following modes;- Enforcing - policies are enforced
- Permissive - policies are logged
- Disabled
- sestatus
- getenforce
Enable SELinux
$ setenforce 1
$ getenforce
Enforcing
Disable SELinux but still continue logging
$ setenforce 0
$ getenforce
Permissive
These policies are defined for files and processes (yes, running programmes) and each are known as "security context". These can be of scontext (source context) or tcontext (target context). Here are ways you can display security context of;
- Files. ls -Z
- Processes. ps auxZ
A security context have the format
user : role : type : mls
Where
system_u:object_r:httpd_sys_content_t:s0
- user - run as user (e.g. system_u)
- role - run as this role (e.g. object_r)
- type - domain type to run (e.g. httpd_dyd_content_t)
- mls - multi-level security, its hidden if not in use. (Lowest security level with no compartments e.g. s0, s0.c0.c5 to show )
Security contexts as stored as modules in /etc/selinux/targeted/active/modules.
Try these examples;
Compare the different security context results for folder /bin, /home, /media, /etc, /usr, /var, /tmp and /sbin;
$ ls -Z /
system_u:object_r:bin_t:s0 bin -> usr/bin
system_u:object_r:etc_t:s0 etc
system_u:object_r:home_root_t:s0 home
system_u:object_r:mnt_t:s0 media
system_u:object_r:bin_t:s0 sbin -> usr/sbin
system_u:object_r:tmp_t:s0 tmp
system_u:object_r:usr_t:s0 usr
system_u:object_r:var_t:s0 var
Pre-requisites
Install policy makefile, audit2allow and audit2why$ sudo yum install policycoreutils-python
$ sudo yum install policycoreutils-devel
The audit2allow will retrive data from /var/log/audit/audit.log and list existing rules with
$ sudo audit2allow -a
Step 1. Investigation
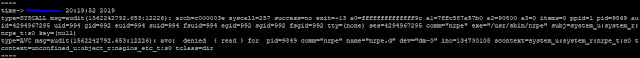
In this example, the application nrpe is not running as it should on a SELinux enabled system. I could start the nrpe process but the output did not work as expected. The tool ausearch and journalctl are used to list the messages during start of a process, where the command is systemctl start nrpe.Its found that the folder could not be open for reading. Listing with the command ls -l showed that it has the correct permission but when ls -Z, then it is seen that there isn't enough access. The process nrpe is by the user nrpe, not nagios. The audit2why is then used to translate the problem into an easier to understand term.
$ sudo ausearch -m avc -c nrpe
$ sudo ausearch -m AVC,USER_AVC,SELINUX_ERR -ts today
$ sudo journalctl -xe
$ ls -l
$ ls -Z
$ ps aux | grep nrpe
$ sudo grep "nrpe" /var/log/audit/audit.log |audit2why
The file localhost.cfg cannot be open for reading
scontext=system_u:system_r:nrpe_t:s0 tcontext=unconfined_u:object_r:nagios_etc_t:s0
The folder nrpe.d cannot be accessed
scontext=system_u:system_r:nrpe_t:s0 tcontext=unconfined_u:object_r:nagios_etc_t:s0
Based on what I have covered before, it can be seen that each have a source context and a target context with their security as user:role:type:mls defined.
Check what context does these nrep and nagios have
$ sudo semanage fcontext -l |grep nagios
/etc/nagios(/.*)? all files system_u:object_r:nagios_etc_t:s0
/etc/nagios/nrpe\.cfg regular file system_u:object_r:nrpe_etc_t:s0
The problem is, nrpe is an application that listens to requires from a remote server to execute Nagios plugins. At NRPE start up, it needs to access customised configuration files located at /etc/nagios/nrpe.d folder.
NRPE, poor thing doesn't have access to sub-folders of /etc/nagios but nagios does.
Step 2: Action
Get the tool audit2allow to generate the required policy.$ sudo audit2allow -i /var/log/audit/audit.log
#============= nrpe_t ==============
allow nrpe_t nagios_etc_t:dir read;
allow nrpe_t nagios_etc_t:file { getattr open read };
Looks like this will allow nrpe to access nagios_etc context type. Generate the required policy and view the policy in local.te
$ sudo audit2allow -i /var/log/audit/audit.log -M local
$ cat local.te
Install the generate local.pp as a module
$ sudo semodule -i local.pp
Check the security policy again and notice that nrpe_t now have access to same type as nagios_etc_t
Stop, and start NRPE process. Check with the log indicate that the error is gone.
$ systemctl stop nrpe
$ systemctl start nrpe
$ journalctl -xe
References:
https://wiki.centos.org/HowTos/SELinux#head-faa96b3fdd922004cdb988c1989e56191c257c01
https://opensource.com/article/18/7/sysadmin-guide-selinux





No comments:
Post a Comment